I don’t know how interesting this is, but I thought I’d throw it up anyways.
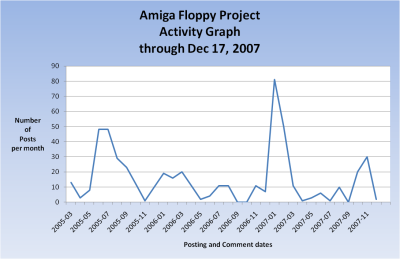
I exported the posts and comments tables from the mysql database, imported into Excel, and then created an activity graph of the blog. I tried correlating the peaks of the graph with specific events, and there really isn’t anything noteworthy that I can find easily. The more I work on the project, the more I post, and the more I post, the more you guys comment.



Has someone hacked your Amiga page? When I visit it, AVG antivirus pops up two warnings: one for JS/Downloader Agent, and one for ‘Exploit.’
Phil,
Can you please be more specific as to where exactly you are getting these warnings?
It could be a false positive, I just checked everything, and everything looks secure to me. I’m going to double check my HTTP logs but I’m running a very current version(albeit not the absolute latest) of wordpress, so it should be secure.
Can you provide the exact URL’s where you saw this? Was it inside wordpress or another page within my site?
Occasionally com_ment sp_am gets through, but I’m running some utilities that do a pretty good job of keeping that out.
Thanks.
Phil,
I REALLY appreciate the heads up on this one.
I tracked the problem down to two posts, one dated 11-15-07, and one dated 10-31-07 where someone from China managed to somehow edit my posts and was doing an in-line iframe which redirected the user to some “wp-stats-php.info” site.
You know, I noticed the redirection(although I was never affected, probably because of script-blockers etc) perhaps over the last week or so. I had been playing with WP-STATS of all things, and thought it was leftover plug-in crap. It wasn’t!
In any event, I’ve edited the posts and removed the offending content.
All my passwords have been changed, but I don’t believe that’s how they got in. I think they used an SQL Injection technique to edit the database directly without passwords.
WordPress.org knows about this, but there hasn’t been any concrete evidence on exactly which versions are/were vulnerable.
https://wordpress.org/support/topic/134928/page/2?replies=38
I’m still trying to track down exact dates/times etc by going through backups and logs.
Thanks again
WordPress released a fix yesterday for the vulnerability that someone used to edit my posts here. I’ve already applied the fix, so at least that hole is closed up.
https://wordpress.org/development/2008/02/wordpress-233/
If you are so interested.